Cyber Threat Intelligence Built for the Future
A cybersecurity platform built to detect what others miss. By analysing global network relationships and behavioural patterns, Silent Push reveals threats long before they reach your perimeter.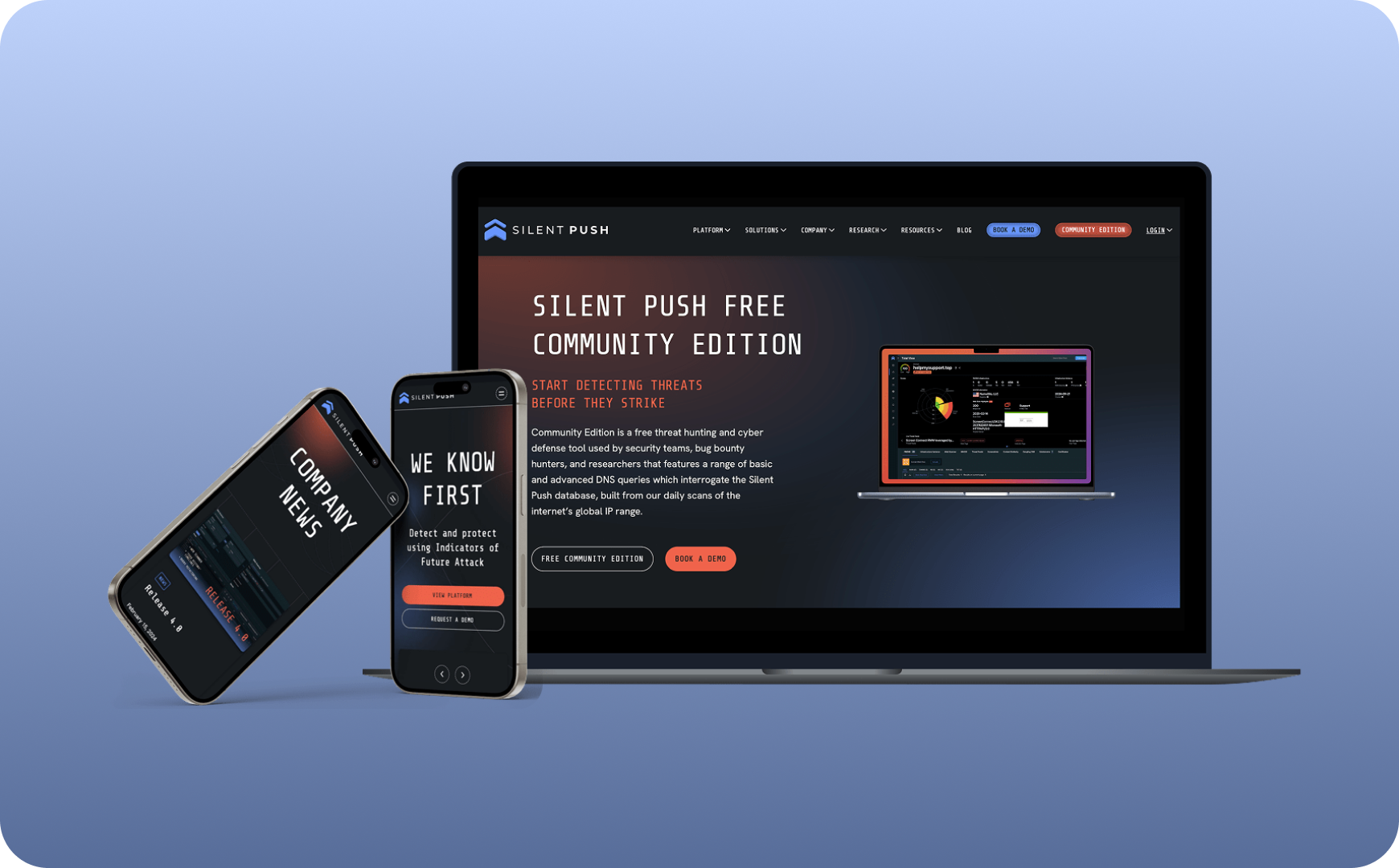
About the Project
Client’s Needs
What We Created
Front-end side
React
Allowed us to easily organise code and supported a component-based approach to development.
HTML/CSS
Used for creating the structure and styling of the website.
JavaScript (ES6+)
Employed for programming client-side logic.
Back-end part
Node.js
Used for executing JavaScript code on the server side.
SQL
For backend data management and retrieval in web applications.
JavaScript (ES6+)
Employed for programming client-side logic.
Platform Features
Infrastructure monitoring
Continuous monitoring modules that analyse infrastructure health and identify vulnerabilities as they emerge.
Attack surface mapping
Comprehensive mapping tools that visualise and track exposed areas across the entire attack surface, enabling stronger defensive decisions.
Phishing prevention
Detection and prevention mechanisms are designed to identify suspicious patterns associated with phishing and social engineering attempts.
Early detection feeds
Intelligence feeds that deliver early warning signals, allowing organisations to assess and react to threats at the earliest stages.
Data enrichment
Enrichment layers that contextualise raw threat data with metadata, patterns, and behavioural indicators for more informed analysis.
Security operation enhancement features
Advanced operational features that streamline investigations, accelerate response workflows, and elevate overall security readiness.
In Conclusion
The delivered platform generates detailed behavioural footprints of attacker Tactics, Techniques, and Procedures (TTPs), helping organisations reduce exposure to financial and reputational risk.
Silent Push produces Indicators of Future Attacks (IOFA) by scanning and enriching global IPv4 data, enabling precise, proactive threat detection before execution.